Phishing protection refers to the tools, strategies, and technologies used to detect and prevent cybercriminals from impersonating your brand, stealing credentials, and defrauding your customers. As attackers move faster and impersonate more convincingly, brands need more than just domain scans or email authentication to stay protected.
Many security and digital teams rely on email filters, takedown services, or brand education to manage phishing risks. But in today’s landscape, those measures only scratch the surface. Brand impersonation has evolved into a fast-moving, multi-channel problem, and most traditional defenses are reacting too late.
This blog explores how leading teams are replacing outdated approaches with real-time, session-aware brand defense – backed by best practices that reflect today’s phishing landscape.
Related: How to Choose the Best Domain Takedown Service
What is phishing protection?
Phishing protection is the proactive identification, detection, and prevention of scams that impersonate a trusted brand to trick users into sharing sensitive information. These scams typically take the form of fake websites, login screens, mobile apps, or typosquatting domains, and often bypass legacy detection methods entirely.
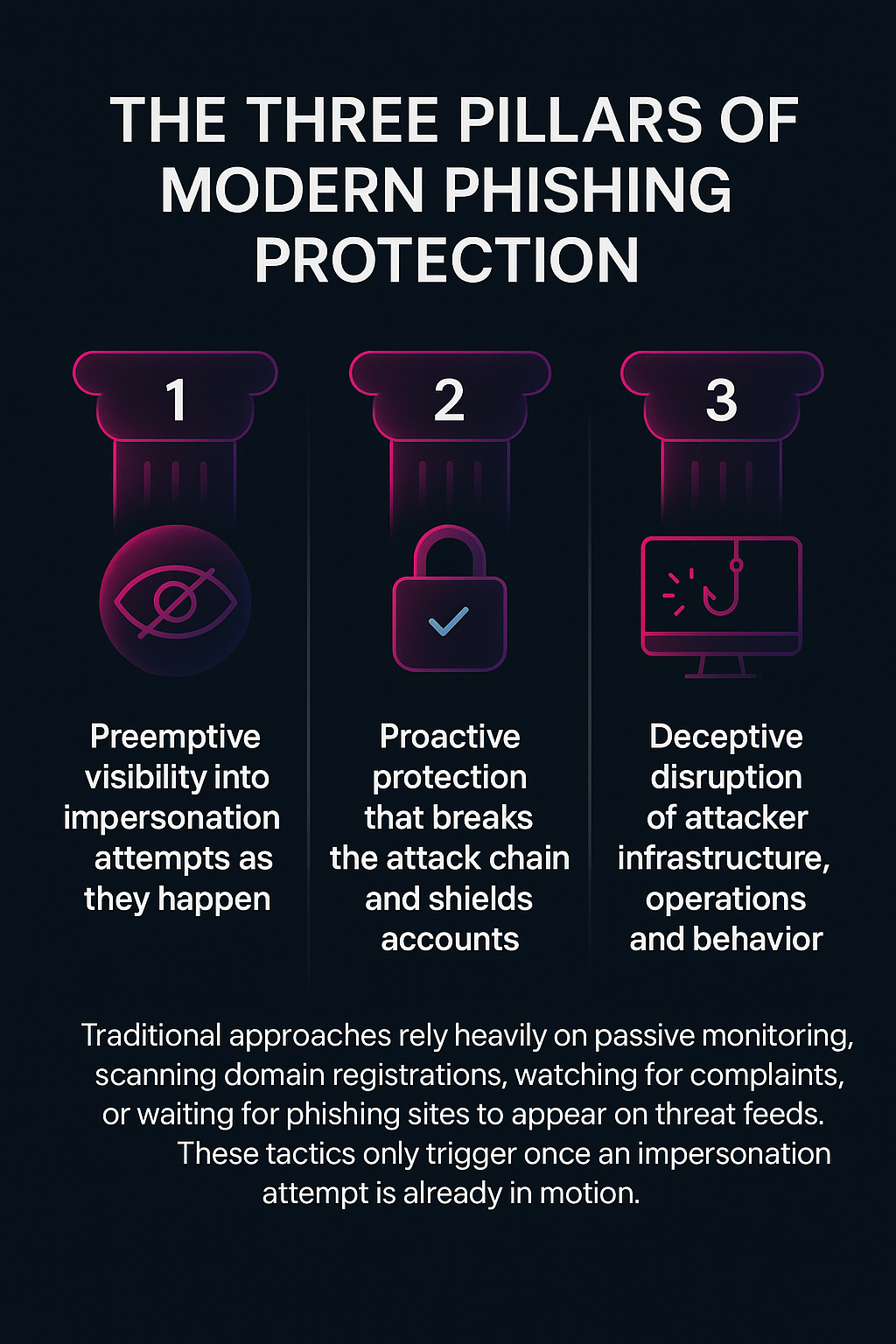
Strong phishing protection includes three core real-time capabilities:
- Preemptive visibility into impersonation attempts as they happen
- Proactive protection that breaks the attack chain and shields accounts
- Deceptive disruption of attacker infrastructure, operations and behavior
For most enterprises, this now requires tools beyond basic DNS monitoring or DMARC enforcement.
Best practices for phishing protection and brand defense
1. Replace passive monitoring with preemptive brand impersonation visibility — starting from the first signals of attack
Traditional approaches rely heavily on passive monitoring—scanning domain registrations, watching for complaints, or waiting for phishing sites to appear on threat feeds. These tactics only trigger once an impersonation attempt is already in motion.
A stronger best practice is to adopt preemptive visibility: the ability to detect signs of brand impersonation during the earliest stages of attack preparation. That includes monitoring signals that originate on your own legitimate site—where attacker behavior often reveals itself first.
To enable preemptive visibility:
- Identify self-built phishing sites or those created using known cloning kits
- Monitor for suspicious developer tool activity, which often signals preparation for website cloning
- Detect spoofed domains and SSL certificate mismatches as early indicators of infrastructure abuse — before users are targeted
2. Prevent phishing site access in-session, act before compromise begins
Most phishing protection measures activate too late, only after a phishing site has been reported, listed on a threat feed, or taken down. But once a scam is live, even a short delay can result in account compromise or data theft.
A best practice is to implement in-session protection that identifies and responds to spoofing attempts the moment a user interacts with them. Real-time visibility allows you to act before stolen credentials are used or users fall victim.
- Deploy Red Alerts that warn users upon landing on a detected phishing page
- Use decoy credential injection to replace user-submitted data with fake credentials, rendering stolen data useless
- Flag and, when applicable, lock out repeat attackers or suspicious devices attempting to access your genuine login portals
This in-session defense is critical, especially when phishing campaigns target high-value accounts or spread rapidly through SMS or paid search ads.
3. Detect phishing referrals and SEO poisoning, uncover the invisible threat
Not all phishing attacks begin with a suspicious email. Many now exploit less visible vectors, such as search engine manipulation and third-party redirect abuse, that bypass traditional email filters and threat detection tools.
A best practice is to track how users arrive at your site. Analyzing referral traffic and SEO patterns can reveal when impersonators are hijacking your brand presence or redirecting users into scams.
- Redirects from compromised or low-reputation websites
- Search results manipulated through SEO poisoning, where fake sites outrank the real ones
To counter this:
- Analyze inbound traffic for unusual referral patterns
- Track first-time referrers that spike suddenly, especially around login flows
- Detect SEO manipulation early by monitoring which keywords are being hijacked to promote impersonator domains
4. Extend protection to mobile and social platforms, phishing has moved beyond web
Today’s phishing attacks don’t stop at websites. Threat actors increasingly publish fake mobile apps, impersonate brands in paid ads, and run scams across social platforms.
Related: How to Detect and Stop Fake Mobile Apps Before They Lead to ATO
A best practice is to treat mobile and social channels as primary phishing vectors. Proactively monitoring these environments helps detect impersonation attempts early and protect customers across every digital touchpoint.
- Monitor Google Play and Apple App Store daily for apps misusing your brand name or assets
- Scan paid ad platforms for impersonation of your domain or branding, and detect traffic into the real site that originates from fraudulent ad campaigns
- Use brand monitoring tools to detect unauthorized profiles on platforms like Facebook, Instagram, LinkedIn, and Telegram
The phishing landscape is channel-agnostic. Your protections should be too.
Related: Automated Brand Impersonation Protection: How It Works (and Why It Matters Now)
5. Integrate phishing protection across teams, silos delay response and resolution
Fragmented phishing protection efforts often miss the full picture. SOC teams may detect unusual login behavior without knowing it originated from a phishing campaign, while fraud teams may lack device-level insight.
A best practice is to integrate phishing visibility across fraud, SOC, and digital teams. Shared signals and unified workflows improve detection accuracy, shorten response times, and enable coordinated remediation.
- Share device fingerprints and phishing indicators with fraud teams to strengthen detection models
- Alert SOC analysts to phishing-driven login attempts and device anomalies
- Equip digital teams with visibility into ad, referral, and site spoofing threats that affect user experience and conversions
Related: How to Run a Domain Spoofing Check (and Stop Fake Sites Before They Hurt You)
When protections operate in isolation, threats fall through the cracks. When integrated, phishing defense becomes a source of intelligence.
How Memcyco helps fill the phishing protection gap
Memcyco’s real-time impersonation protection delivers what most brand defenses lack: visibility into individual victims, session-level attack detection, and automated disruption of phishing attempts as they unfold.
Here’s how Memcyco enhances phishing protection:
| Memcyco Capability | What It Detects | Benefit |
| Website Cloning and Spoofing Detection | Cloned or partially replicated brand sites, including visual replicas and structural imitations | Early warning of active impersonation attempts before users interact with fraudulent pages |
| Developer Tools Reconnaissance Detection | Attempts to inspect or copy original site code | Exposes early signs of phishing campaign preparation |
| Suspicious Hostname Detection | Lookalike domains and SSL certificate mismatches | Identifies deceptive infrastructure before it is weaponized |
| Decoy Credential Injection | Stolen credentials entered on fake sites | Turns scams into honeypots; disrupts the ATO chain by rendering harvested data unusable |
| Real-time Red Alerts | Customers accessing spoofed or fake sites | Warns victims instantly, limits damage, and enables immediate response |
| Suspicious Device Blocking | New or untrusted devices attempting account access after phishing | Prevents repeated attack attempts from devices previously linked to malicious activity |
| SEO Poisoning Defense | Fake pages designed to manipulate search rankings and impersonate your brand | Prevents malicious search engine manipulation from elevating phishing sites in search results |
These capabilities operate at the browser level, giving Memcyco unique visibility into the referral paths, device behaviors, and login attempts that signal phishing in progress, even when phishing sites are not listed in any threat feed or blocklist.
Security teams gain insights into which devices are running phishing campaigns. Fraud teams can detect when credential misuse originates from a fake site. Digital teams gain protection without degrading user experience or requiring end-user changes.
Memcyco doesn’t just detect impersonation, it helps you preempt damage, respond before compromise, and secure customer trust.
Final Thoughts: Rethinking Phishing Protection
Phishing protection has shifted from a passive, background safeguard to a front-line brand defense capability. Modern attackers move quickly, exploit multiple channels, and adapt in real time. Organizations that continue relying solely on legacy methods – like takedowns, static blocklists, and awareness campaigns – accept unnecessary exposure.
Enterprises that adopt real-time, session-aware protection can detect and disrupt impersonation activity before credentials are stolen or customers are misled. This proactive stance closes the visibility gap, strengthens customer trust, and positions the brand ahead of evolving threats across web, mobile, and search.
FAQ: Phishing Protection and Brand Impersonation
What is the best way to stop phishing sites from targeting my brand?
Use a solution that monitors real-time impersonation attempts, issues in-session alerts, and disrupts phishing campaigns before users are harmed. Traditional takedowns are no longer fast enough.
Can phishing sites be detected without code on the attacker’s site?
Yes. Memcyco detects phishing activity through browser-layer signals on your legitimate site, including suspicious referrals, credential misuse, and cloned site fingerprints, without needing access to the phishing site itself.
Related: What to Look for in a Phishing Site Detection and Takedown Solution | Memcyco
How do attackers impersonate brands in search results?
Using a tactic such as SEO poisoning, fraudsters publish fake pages optimized to rank in Google or Bing. Memcyco’s SEO poisoning defense helps prevent these sites from appearing in search engines.
Does Memcyco help protect mobile app users?
Yes. Memcyco detects fake mobile apps published in official stores, monitors for impersonation in mobile ad networks, and secures login flows in native apps through backend telemetry monitoring.
What is brand impersonation in phishing?
Brand impersonation occurs when attackers mimic your digital assets, such as websites, login portals, or mobile apps, to trick users into thinking they’re interacting with the real brand. It’s one of the fastest-growing phishing threats.
How fast does phishing detection need to be?
Instant. The window of exposure for phishing sites is now often under 6 hours. Real-time phishing protection is the only viable path to preventing fraud at scale.
Can phishing protection help with compliance?
Yes. Demonstrating active detection and prevention of impersonation attacks supports compliance with cybersecurity frameworks and industry regulations. It also provides evidence of due diligence in protecting customer data and digital channels.